New Threats on the Road: 3 Modern Ways Thieves Are Stealing Cars
The threat of car theft remains a significant concern for vehicle owners nationwide. According to recent reports, vehicle thefts in the United States have seen an uptick. Certain models, like full-size pickup trucks and popular SUVs, are frequently targeted due to their high demand and valuable parts.
The financial impact of these thefts is substantial, with the average loss per stolen vehicle exceeding $9,000. This includes the vehicle’s value, insurance costs, and the significant inconvenience for victims. Alarmingly, a growing percentage of these thefts now involve sophisticated electronic techniques that bypass traditional security.
Understanding these new tactics is the first step in protecting your investment. It’s no longer just about locked doors and alarms; thieves are leveraging technology to their advantage.
Method 1: Relay Attack

One of the most alarming methods used by car thieves today is the relay attack, which we’ve reviewed before on the Compustar blog. This sophisticated technique exploits vulnerabilities in keyless entry systems. It’s estimated that over 90% of vehicles with push-to-start ignitions are susceptible to this type of theft.
Here’s how it works: Thieves use electronic devices to amplify and relay the signal from your key fob, even if it’s inside your home. This tricks the car into thinking the key is nearby, allowing them to unlock and drive away in your vehicle.
Method 2: CAN Bus Attack, or “Injection”, Through the Headlamp
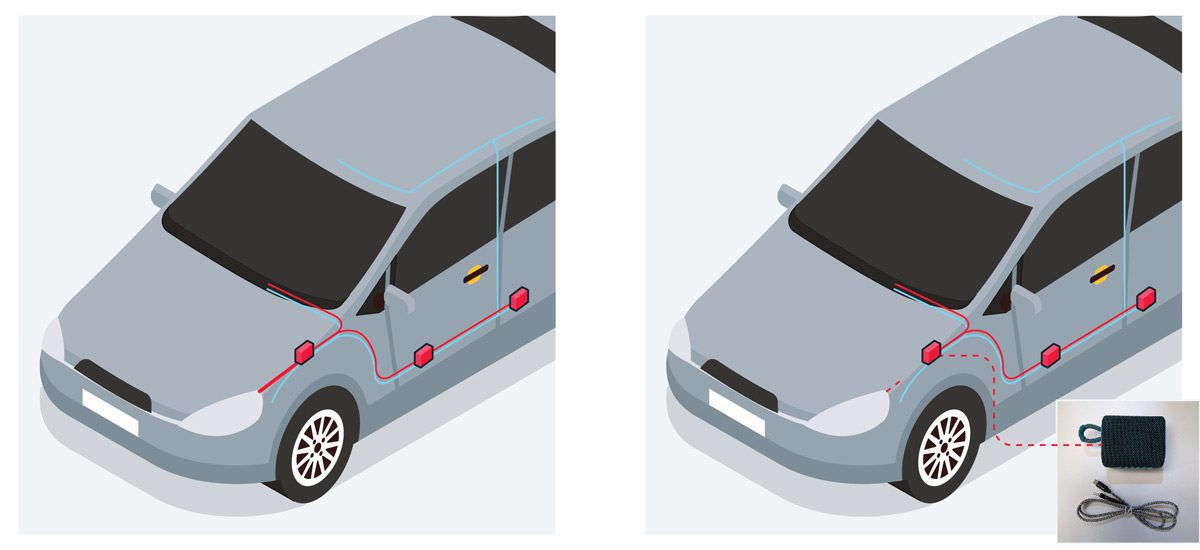
Another emerging method involves exploiting the car’s Controller Area Network (CAN) bus. This internal communication network controls various functions in your vehicle. Thieves have discovered that they can access the CAN bus through the headlamp wiring in certain vehicles, particularly Toyota and Lexus models.
By connecting to the CAN bus, thieves can bypass security systems and gain control of the vehicle, allowing them to start the engine and drive off.
Method 3: Key Cloning Attack
Another concerning method thieves are employing is key cloning. This technique involves creating an unauthorized secondary key for your vehicle. This can be achieved by connecting a specialized computer device to the On-Board Diagnostics II (OBD-II) port, typically located under the dashboard. Using the publicly visible Vehicle Identification Number (VIN) and readily available key remote generator tools, similar to those used by dealerships and locksmiths, they can program a blank key fob to function as a legitimate key for your car.

It’s also important to note that another method of key cloning occurs if a thief can briefly gain physical access to your key fob. Using specialized devices, they can literally clone the key’s signal, allowing them to unlock and start your vehicle as if they had the original.
Both of these key cloning methods are particularly alarming as they bypass traditional security measures without requiring forced entry or the manipulation of wireless signals in the same way as a relay attack.
How Compustar Thwarts These Theft Efforts
While your vehicle’s factory system may not block the modern methods used by car thieves, Compustar offers a range of security solutions that have been proven to stop these threats.
- Starter-kill: A standard feature of most Compustar alarm systems is a starter kill. Prevents unauthorized ignition attempts when the alarm is armed. Even if thieves manage to bypass other security measures, they won’t be able to start the car. Think of starter kill as dual-authentication for your vehicle. In order to compat relay attacks, specifically, Compustar security systems now offer an exclusive feature called “Secure Push-to-Start”!
- Alarm notifications: Sends real-time alerts to a 2-way remote or the Dronemobile app, notifying you immediately of any attempted break-ins or theft. In addition to detecting start attempts, Compustar systems can monitor for impact, tilt, glass-breakage, and unauthorized entry.
- GPS tracking: Enables fast vehicle recovery with the help of the authorities. In the unfortunate event that your car is stolen, you can track its location and assist law enforcement in its recovery.
Ultimately, investing in vehicle security is a wise decision. It’s similar to buying insurance – a relatively small upfront cost to protect against a potentially huge financial loss and the associated stress and inconvenience.
How to Buy
To find the right Compustar system for your vehicle and needs, you have two options:
- Contact your nearby Compustar dealer and installer: They can provide expert advice and professional installation.
- Use our Compustar System Builder: This online tool helps you find the perfect system for your specific vehicle and security requirements.
If you would like to learn more about how Compustar is keeping vehicles and people safe, check out our Youtube and Instagram pages for videos and more!
Sources:




